Cyber Security Best Practices – Outsmarting Hackers and Scammers
The goal of this page is to better prepare you to recognize the signs of a scam, and to identify signs you may have been hacked.
Scammers and hackers will prey on your sense of urgency and worry, pushing you to take fast actions that give them an opportunity to access your personal information. ALWAYS take your time, verify sources, and stay suspicious!
Common Scams
Phishing –
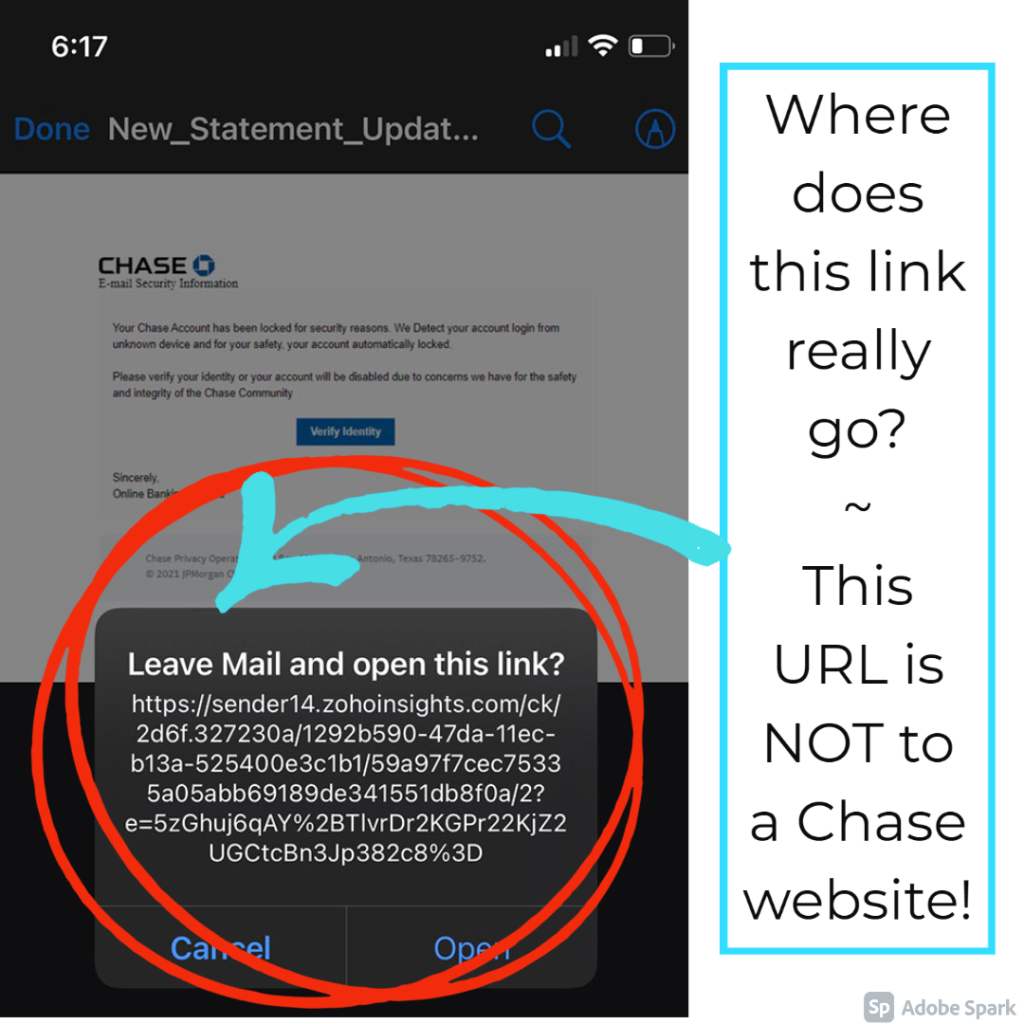
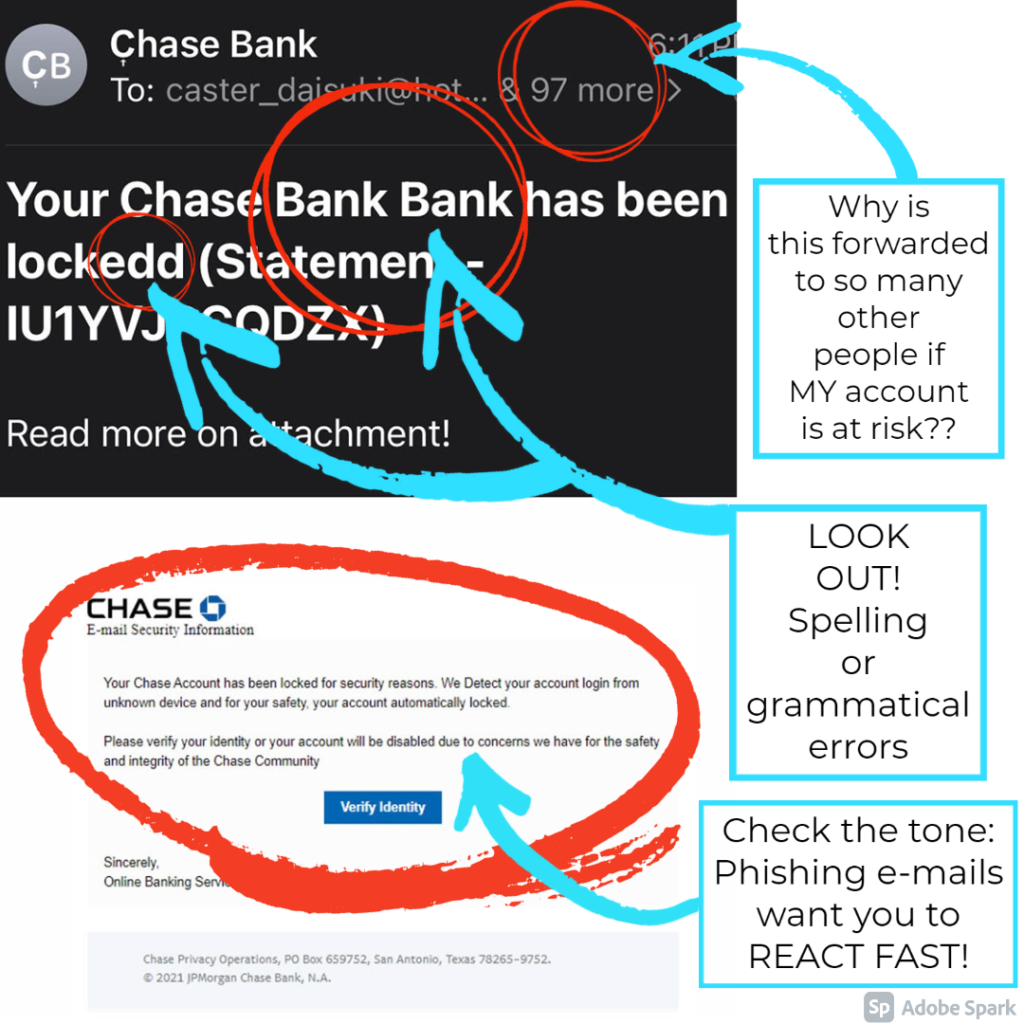
Does this email look “phishy” to you? Phishing is almost as old an email itself, but it still tricks people everyday. Phishing emails seem to come from companies you know and trust urging clients to reveal personal information like passwords or credit card info.
Below we have highlighted some key areas that give this email away as a Phishing attempt; the URL is not to a chase website, the email is forwarded to 97 others even though it proclaims to be about YOUR banking accounts, the spelling and grammar is unprofessional, and the key tip is the sense of urgency they are trying to convey.
You can report an attempted Scam HERE with the Federal Trade commission.
Social Engineering –
Social Engineering describes the use of deception to manipulate people into performing actions like clicking malicious links or divulging personal confidential information. Scammers will masquerade as a trusted friend sending you a funny video, or as a grandchild calling in need, so you let down your guard and they can take advantage.
There is no harm in calling that old friend to see if they really did send you a funny video, or calling that grandchild’s knows phone number, to VERIFY the source and protect yourself against bad actors.
You can report an attempted Scam HERE with the Federal Trade commission.

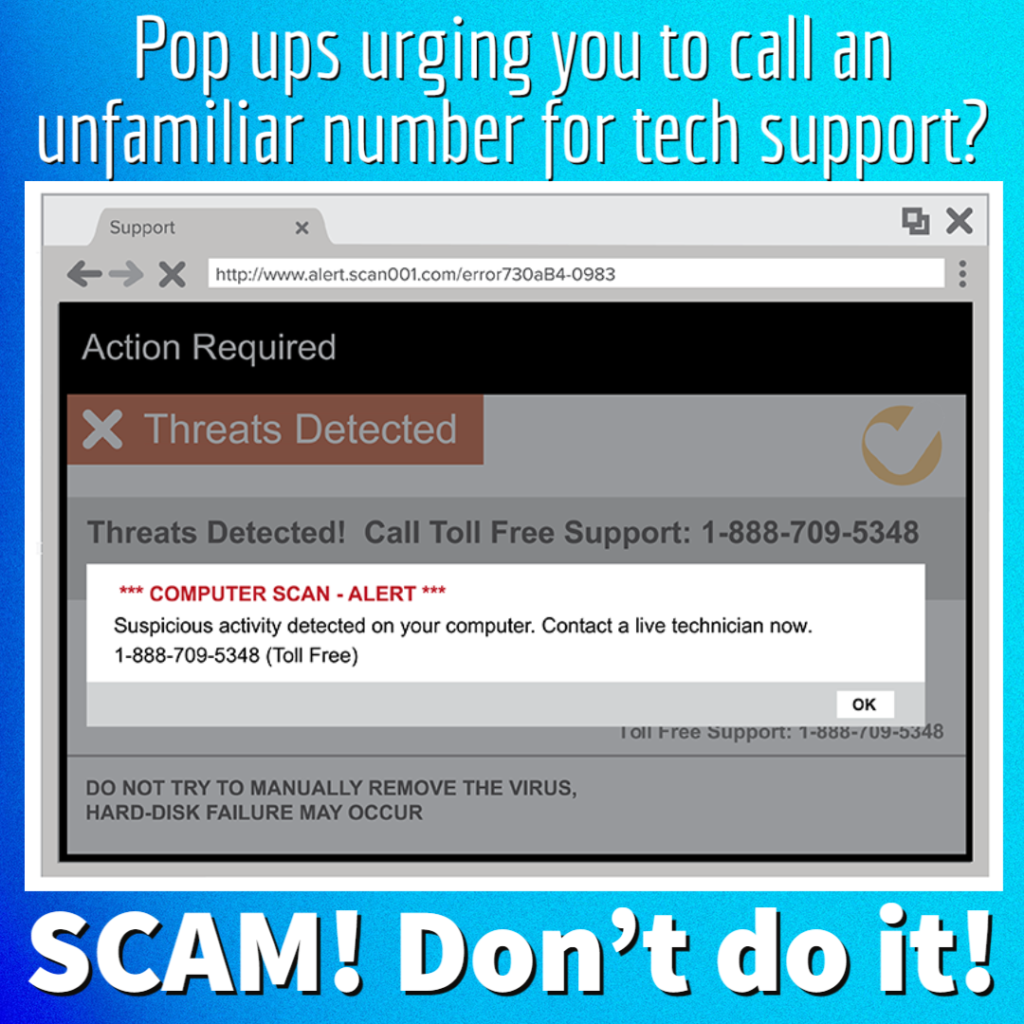
Tech Support –
Tech Support scams can appear on the computer with alarming pop ups, through telephone calls, or by email. Scammers will impersonate a support person from a trusted source, like Microsoft or your banking institution, and trick you into revealing personal confidential info or even giving them remote access to your device!
A tech support call you were not expecting is a SCAM! Remember to NEVER let a stranger remotely access your computer!
You can report an attempted Scam HERE with the Federal Trade commission.

Customer Support Scam
Look out for FAKE Customer Service numbers!!! Scammers & Hackers will masquerade as customer service representatives for legitimate companies to steal your personal & banking information. Avoid pitfalls like this with services like GetHuman.com!

Computer Solutions recommends this site as a free resource to verify the correct Customer Service number for major companies. Already dealing with a scam or hack? Call Computer Solutions today for remediation! We are always happy to answer any questions, call us at 860.239.0708 or email us at info@connecticutCS.com.
What is Ransomware?
Ransomware is a particularly nasty way to take control of someone’s computer and lock out the true user from their important data. Hackers who implement ransomware will lock down your computer, encrypt your data, and demand you pay a hefty ransom before (hopefully) returning your computer’s control over to you.

With this type of hack, data recovery is not always possible, so your best offense is a strong defense.
We recommend having a secure, versioned backup capable of having multiple copies from different times. This is the easiest way to outsmart ransomware, as the backup provides a copy of the computer before it was infected. We are happy to set you up with the right back up for your needs, contact us HERE.
To report a ransomware attack, click HERE.

Are you a “do IT yourselfer”?
Carbonite has multiple solutions tailored for individual computers, servers, small and medium sized business. Follow this link to sign up for Carbonite.

General Rules of Cyber Security
As a rule of thumb, your banking institution will never ask for your passwords. Your computer will never push you a pop up with a tech service number, and a reputable business will not ask for payment in cryptocurrency.
Do not connect to unknown devices. Carry out regular back us and patches. Use STRONG PASSWORDS. Never click on suspicious links, and if it seems too good to be true, it probably is!
Remember, a scammers #1 tool is YOUR PANIC!

What to do about Pop-ups?

Pop ups can be a gateway to the danger zone. You may think clicking the “close”, “no” , or “x” buttons shuts them down, but hackers can program these buttons to take any action, including downloading a virus! So when you click “no” to decline the pop ups offering you could be falling into their trap. When you see a pop up, DO NOT CLICK ANYTHING. The safe way to shut down these pop ups is, for windows, use the ALT and F4 keys simultaneously, and for Mac, use Option, Command, and Esc simultaneously.
Computer Solutions – We Can Help!
We offer a variety of services aimed at preventative care to protect your devices from certain threats. We also offer services if you have already been compromised, or even suspect something isn’t quite right. In the world of computers, “better safe than sorry” should be your motto! Contact us for a free consultation and estimate by phone. If you have questions or have already been hacked, call Computer Solutions at 860.239.0708. We are experts at virus removal, data recovery, and can create preventative back ups so your data is protected. Stay safe out there!
Computer Solutions also offers Training/Tutoring on how to protect yourself online & how to tell if something is a scam


